
| This is a work in progress. Watch for updates to this post and the full article. (Last updated March 18, 2021) |
Cybersecurity risk management for supply chains with multiple vendors is complicated. Each vendor is clearly responsible for its own system, but who minds the overall end-to-end concerns? This article asserts that coordination across organizational boundaries is needed to assess and mitigate cybersecurity risks in remote patient monitoring (RPM) systems.
Examples of network-connected RPM devices include wearables (e.g., smart watches), glucose monitors, pacemaker monitors, blood pressure cuffs, pulse oximeters, continuous positive airway pressure (CPAP) machines, scales, and more. Such devices are part of the family of the Internet of Things (IoT).
A 2019 survey of physicians showed “Two in three, or 68 percent, of physicians surveyed strongly intend to use remote patient monitoring technology…” However, the survey report also indicates “Health care professionals view data security as the main barrier to technology uptake.”[1]
The majority of recent cybersecurity analysis for medical devices has focused on devices used within hospitals and clinics. Cybersecurity for RPM is different in a number of ways.
RPM is a “system of systems” – a physical and digital chain consisting of devices connected to networks, connected to other networks. Typically, there are multiple stakeholders involved in the provision and operation of these systems These include device manufacturers that depend on a supply chain for software and hardware components, communications networks, data integrators, and the clinicians who are the ultimate users of the data (Figure 1). Also, various interfaces with humans, including patients, caregivers, developers, network engineers, and system administrators.
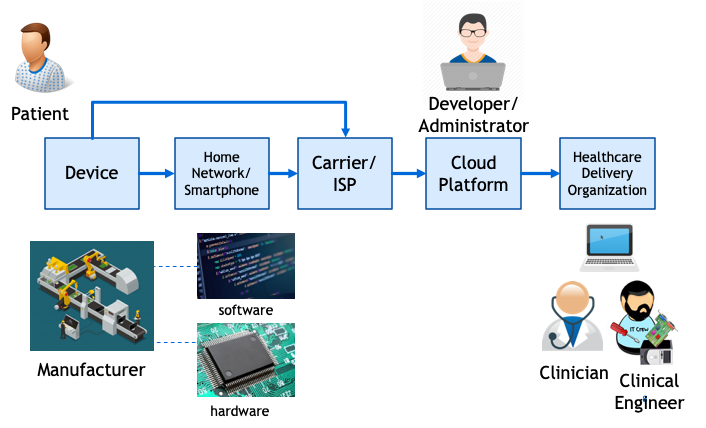
Attacks on healthcare delivery organization (HDO) networks via device or interim partner vulnerabilities are a bigger concern than attacks on individual devices. This is because more harm can be done if a healthcare delivery organization network is compromised. Attacks on these networks can not only result in theft of personally identifiable information, but also interruption of service, such as what occurs in a ransomware attack.
In a RPM digital supply chain with multiple vendors involved, it is necessary to take a “trust, but verify” approach. Clauses can be put in a contract or a “Business Associate Agreement” to require a supplier/partner (vendor) to maintain a good cybersecurity posture, but it is unlikely that the vendor can absolutely guarantee protection. When only written assurances of “best efforts” to prevent cybersecurity incidents are provided, it behooves the buyer/user to perform due diligence and monitor whether these efforts are effective.
One possible solution is for the healthcare delivery organization that is the receiver of the data to oversee the end-to-end process. Alternatively, the data platform vendor that consolidates, analyzes, and formats the data may be in a position to provide the needed coordination. On the other hand, it is difficult to imagine how device manufacturers could coordinate all of the stakeholders.
As a final thought, remember that the ever-changing cybersecurity landscape means it may not be possible to anticipate and mitigate all threats. In the event an incident occurs, there needs to be a plan to respond and recover. In an environment with multiple vendors, response coordination has to be planned and rehearsed before something happens. The objective is to make sure the entire remote patient monitoring system is resilient.
If you work for a health care delivery organization that is on the receiving end of a remote patient monitoring system, what are you doing to make sure all of the components in that system are secure and that you are ready to respond to problems?
If you are one of the vendors in remote patient monitoring system, what are you doing to make sure your upstream and downstream partners in the system are secure?
If you are not sure how to do this, you’ll probably want to obtain assistance to reach out to each of the organizations that comprise the end-to-end system and figure out an approach to make sure a holistic security framework is conceived and implemented.
* * *
David Snyder is a cybersecurity professional experienced at facilitating discussions among ecosystem members, analyzing complex processes, and orchestrating cross-functional and cross-organizational efforts.
Inquiries: https://42tek.com/contact/
[1] CTA Survey Finds High Demand for Remote Patient Monitoring Devices, 11 April 2019, https://www.cta.tech/Resources/Newsroom/Media-Releases/2019/April/CTA-Survey-Finds-High-Demand-for-Remote-Patient-Mo#/


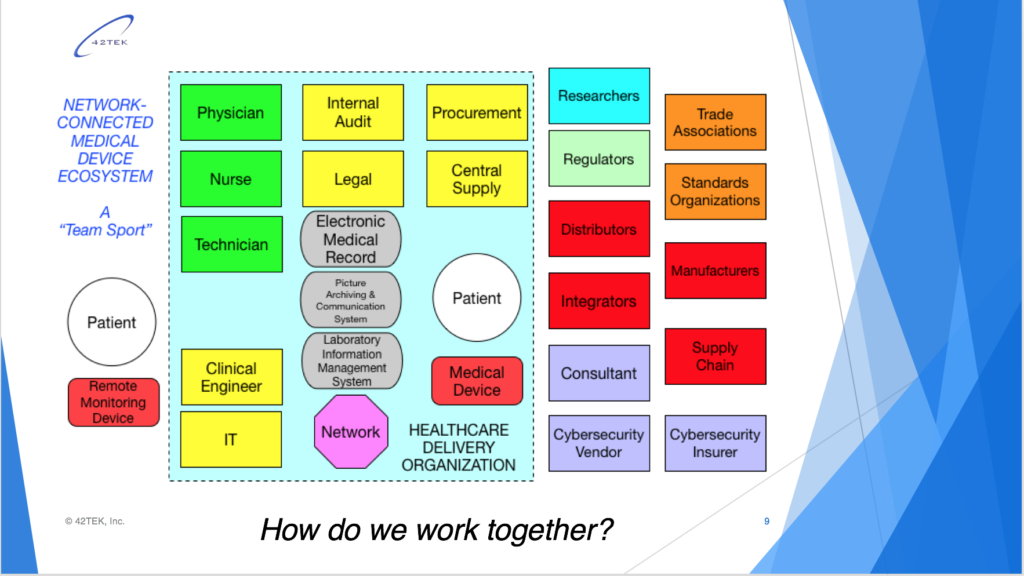
 My session addressed security topics in medical device design and manufacturing, usage in hospitals, remote monitoring, and related legislative, regulatory, and standards initiatives. Bill Saltzstein of
My session addressed security topics in medical device design and manufacturing, usage in hospitals, remote monitoring, and related legislative, regulatory, and standards initiatives. Bill Saltzstein of